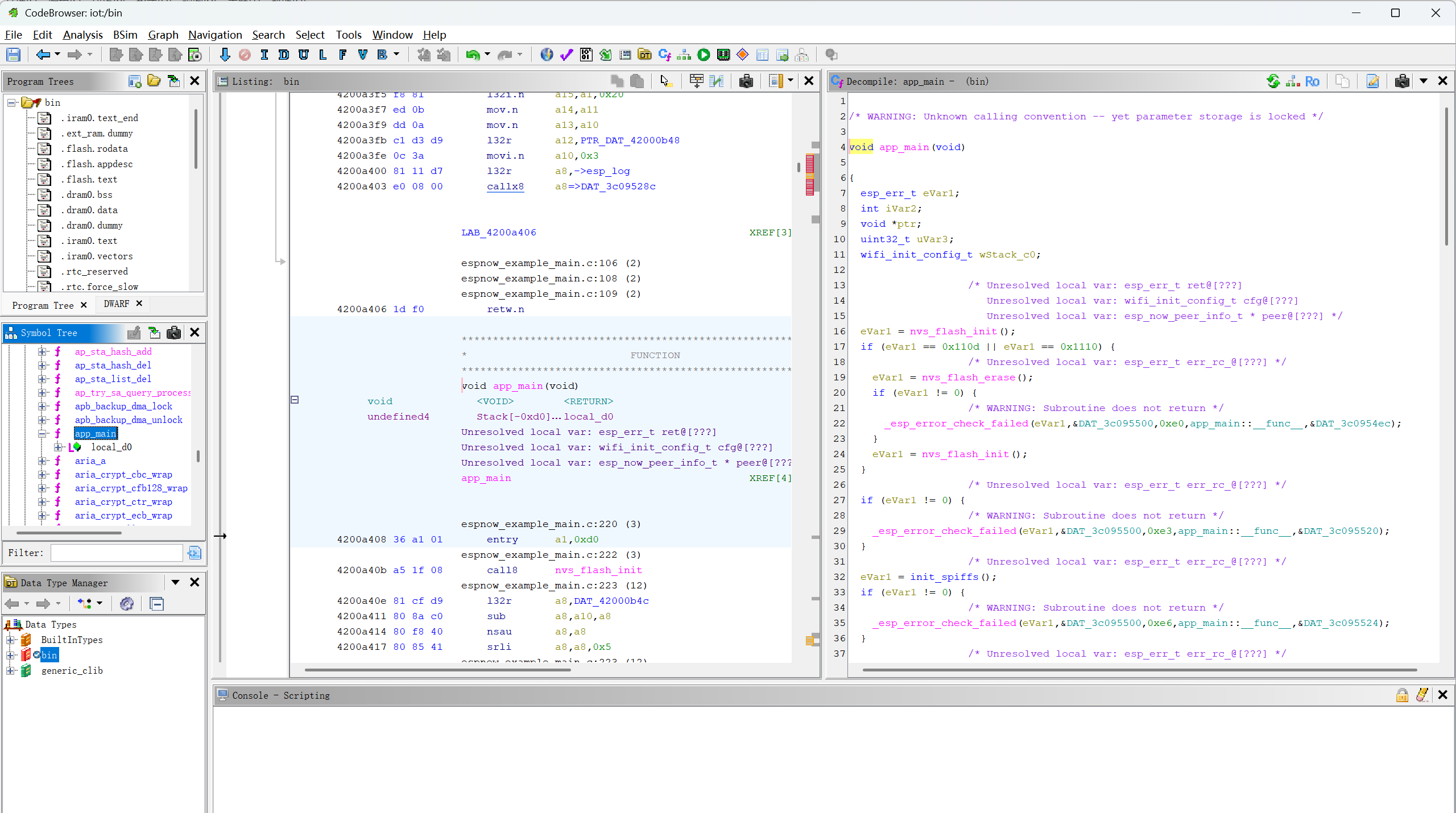
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
|
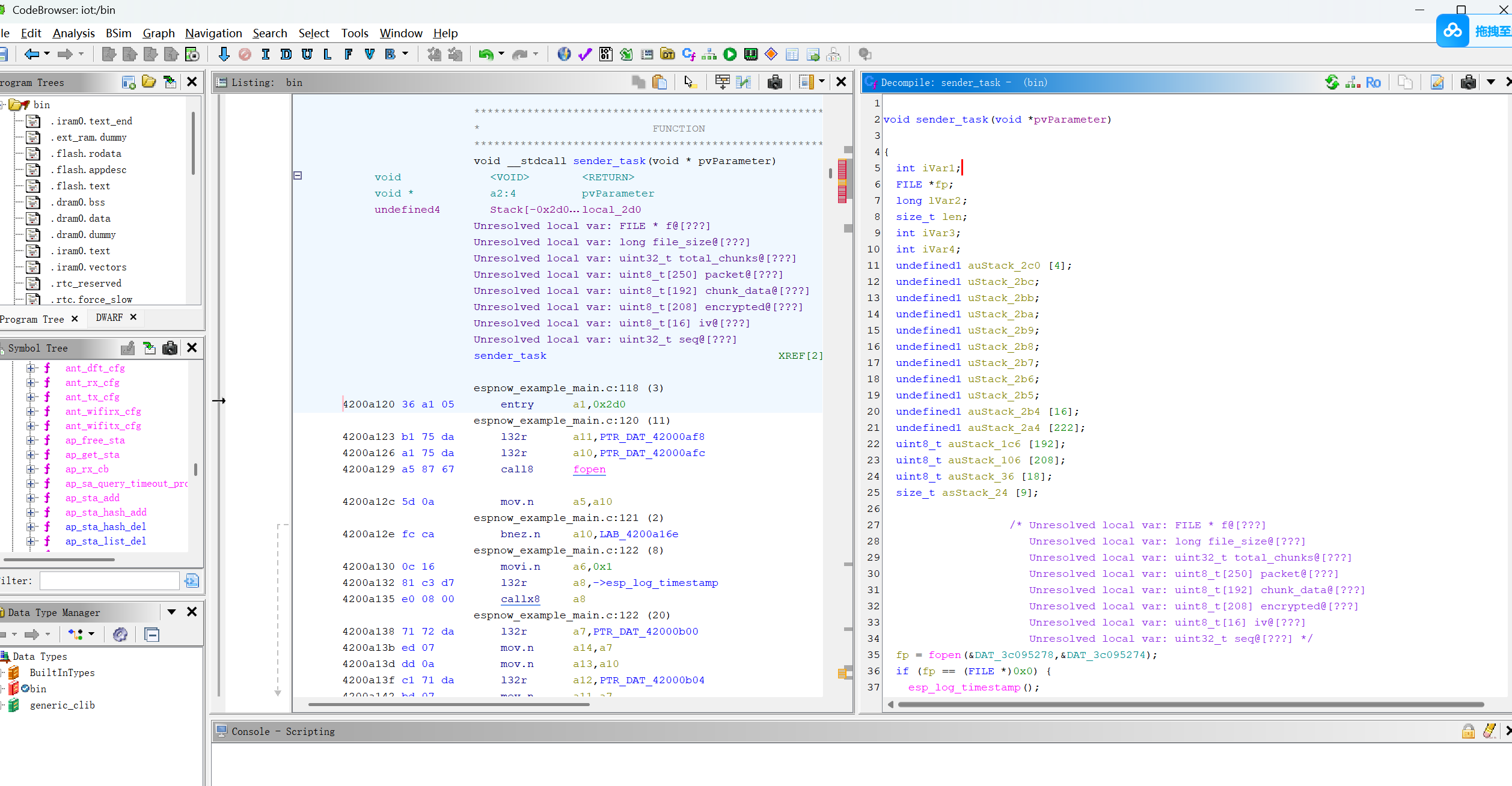
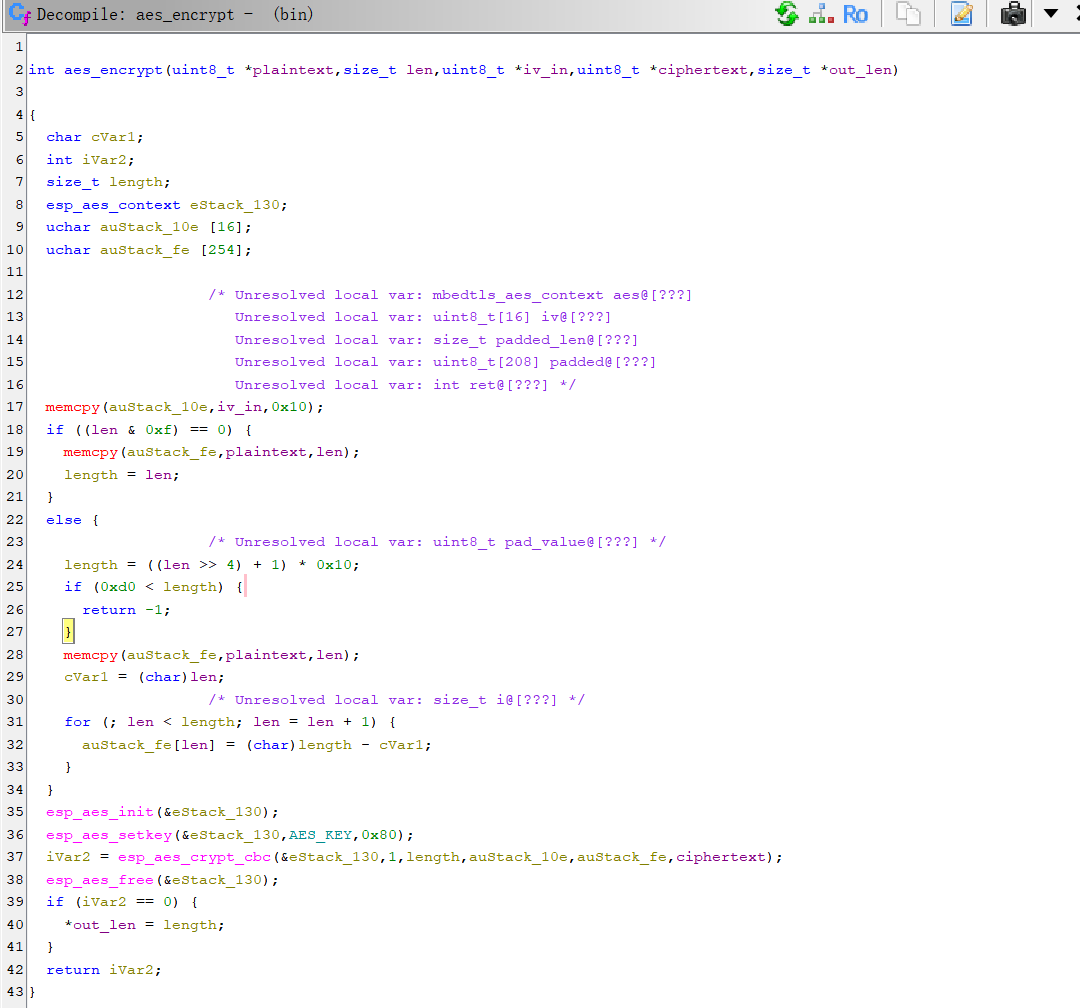
void sender_task(void *pvParameter)
{
int iVar1;
FILE *fp;
long lVar2;
size_t len;
int iVar3;
int iVar4;
undefined1 auStack_2c0 [4];
undefined1 uStack_2bc;
undefined1 uStack_2bb;
undefined1 uStack_2ba;
undefined1 uStack_2b9;
undefined1 uStack_2b8;
undefined1 uStack_2b7;
undefined1 uStack_2b6;
undefined1 uStack_2b5;
undefined1 auStack_2b4 [16];
undefined1 auStack_2a4 [222];
uint8_t auStack_1c6 [192];
uint8_t auStack_106 [208];
uint8_t auStack_36 [18];
size_t asStack_24 [9];
fp = fopen(&DAT_3c095278,&DAT_3c095274);
if (fp == (FILE *)0x0) {
esp_log_timestamp();
esp_log((esp_log_config_t)0x1,&DAT_3c09528c,&DAT_3c095298);
esp_log_timestamp();
esp_log((esp_log_config_t)0x1,&DAT_3c09528c,&DAT_3c0952c8);
vTaskDelete((TaskHandle_t)0x0);
return;
}
fseek(fp,0,2);
lVar2 = ftell(fp);
fseek(fp,0,0);
iVar1 = (lVar2 + 0xbf) / 0xc0;
esp_log_timestamp();
esp_log((esp_log_config_t)0x3,&DAT_3c09528c,&DAT_3c095314);
esp_log_timestamp();
esp_log((esp_log_config_t)0x3,&DAT_3c09528c,&DAT_3c095350);
esp_log_timestamp();
esp_log((esp_log_config_t)0x3,&DAT_3c09528c,&DAT_3c095378);
esp_log_timestamp();
esp_log((esp_log_config_t)0x3,&DAT_3c09528c,&DAT_3c09539c);
esp_log_timestamp();
esp_log((esp_log_config_t)0x3,&DAT_3c09528c,&DAT_3c095314);
iVar4 = 0;
do {
while( true ) {
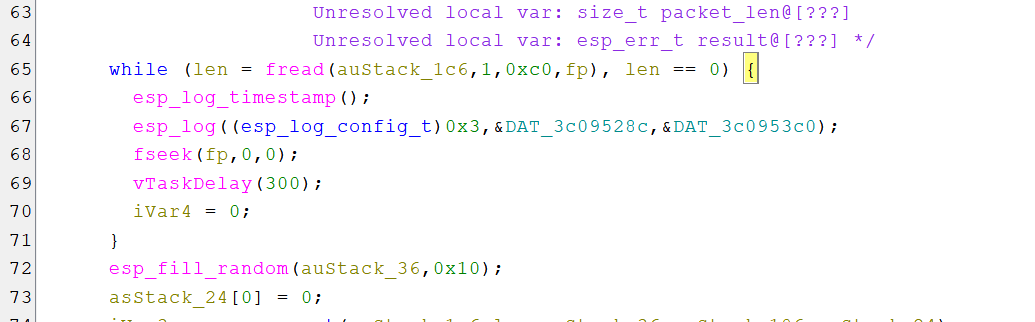
while (len = fread(auStack_1c6,1,0xc0,fp), len == 0) {
esp_log_timestamp();
esp_log((esp_log_config_t)0x3,&DAT_3c09528c,&DAT_3c0953c0);
fseek(fp,0,0);
vTaskDelay(300);
iVar4 = 0;
}
esp_fill_random(auStack_36,0x10);
asStack_24[0] = 0;
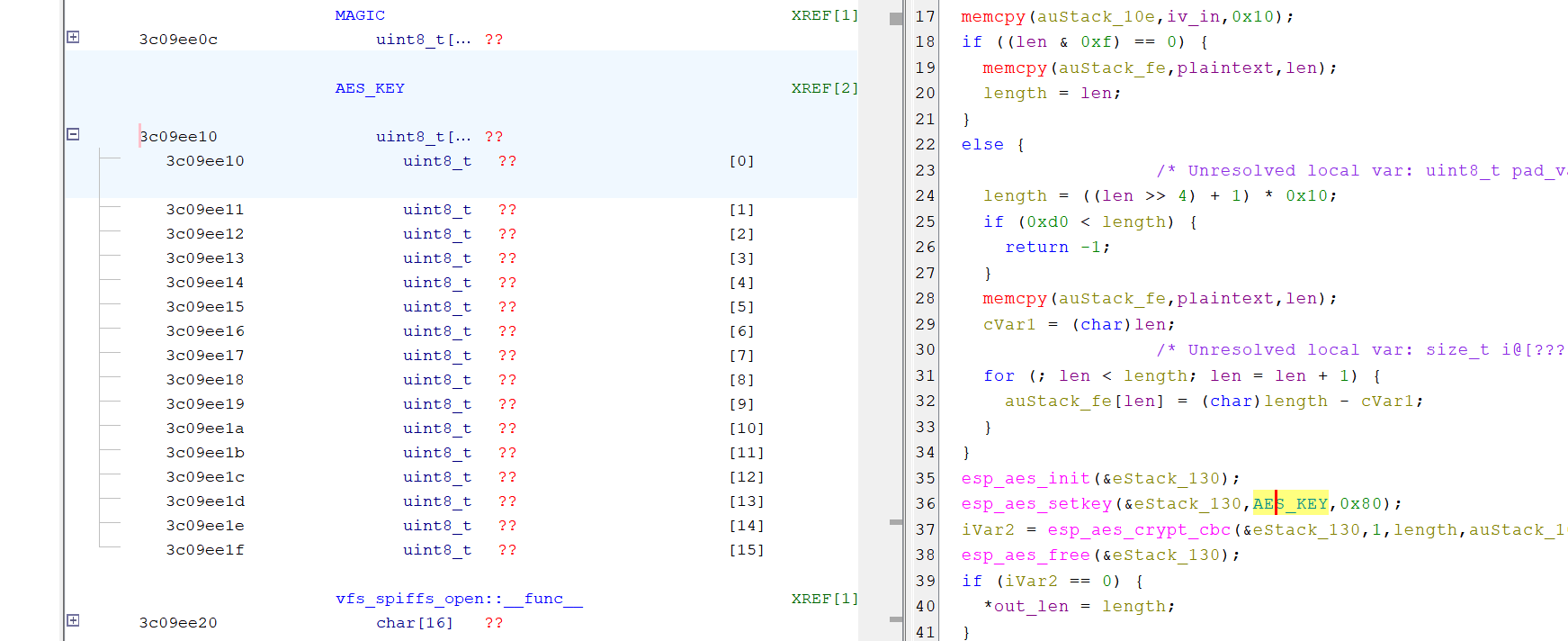
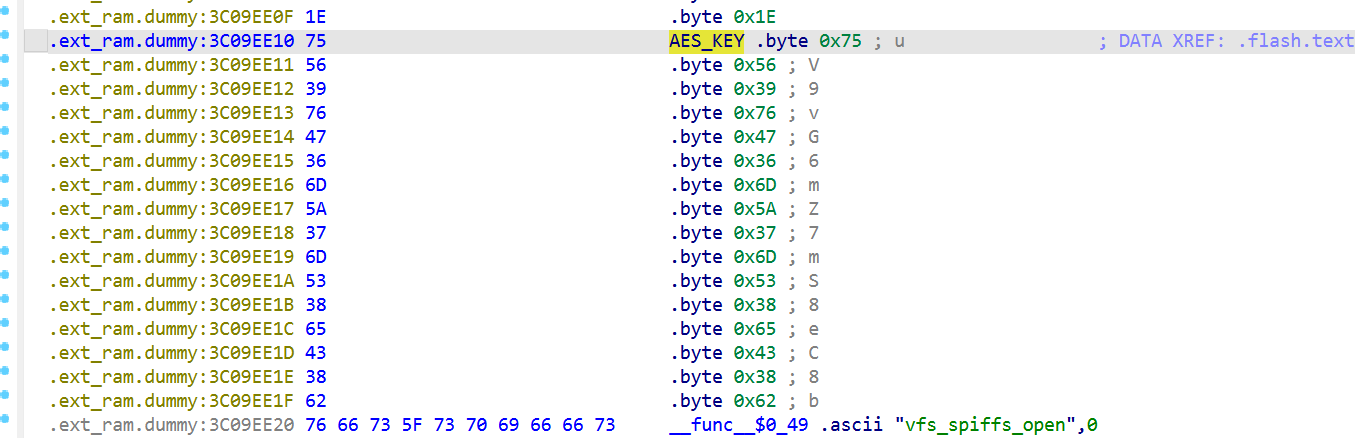
iVar3 = aes_encrypt(auStack_1c6,len,auStack_36,auStack_106,asStack_24);
if (iVar3 == 0) break;
esp_log_timestamp();
esp_log((esp_log_config_t)0x1,&DAT_3c09528c,&DAT_3c0953f8);
}
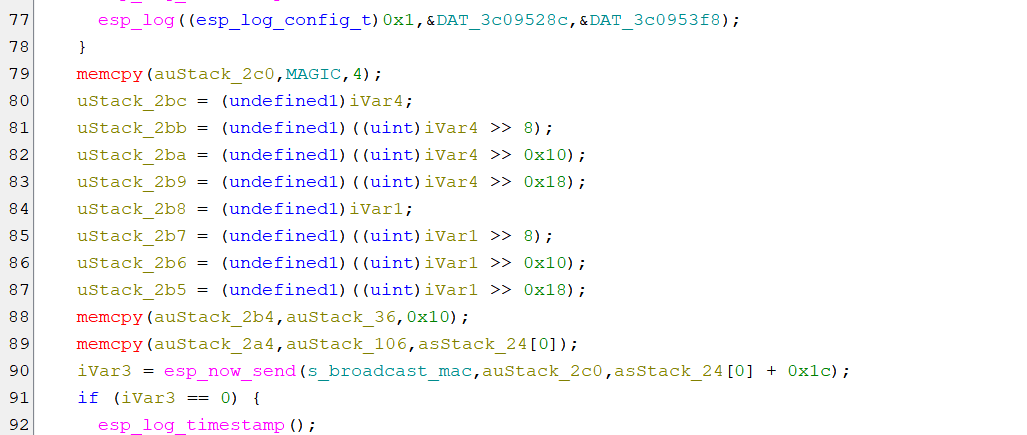
memcpy(auStack_2c0,MAGIC,4);
uStack_2bc = (undefined1)iVar4;
uStack_2bb = (undefined1)((uint)iVar4 >> 8);
uStack_2ba = (undefined1)((uint)iVar4 >> 0x10);
uStack_2b9 = (undefined1)((uint)iVar4 >> 0x18);
uStack_2b8 = (undefined1)iVar1;
uStack_2b7 = (undefined1)((uint)iVar1 >> 8);
uStack_2b6 = (undefined1)((uint)iVar1 >> 0x10);
uStack_2b5 = (undefined1)((uint)iVar1 >> 0x18);
memcpy(auStack_2b4,auStack_36,0x10);
memcpy(auStack_2a4,auStack_106,asStack_24[0]);
iVar3 = esp_now_send(s_broadcast_mac,auStack_2c0,asStack_24[0] + 0x1c);
if (iVar3 == 0) {
esp_log_timestamp();
esp_log((esp_log_config_t)0x3,&DAT_3c09528c,&DAT_3c095428);
}
else {
esp_log_timestamp();
esp_err_to_name(iVar3);
esp_log((esp_log_config_t)0x1,&DAT_3c09528c,&DAT_3c095454);
}
iVar4 = iVar4 + 1;
vTaskDelay(10);
} while( true );
}
|