buuctf
reverse1:
下载附件,解压,将程序用ida打开
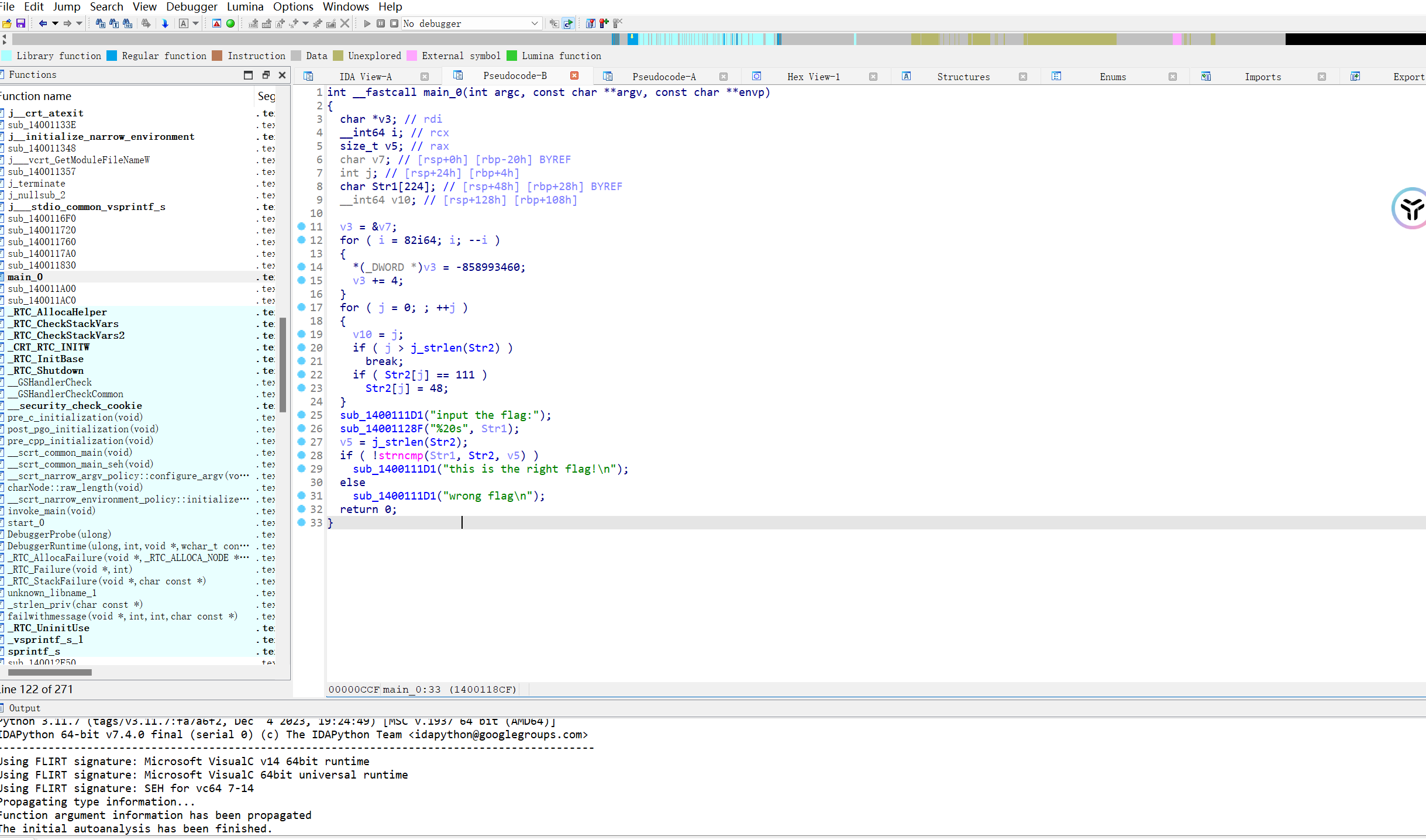
找到主函数,分析得出字符str2为正确的flag
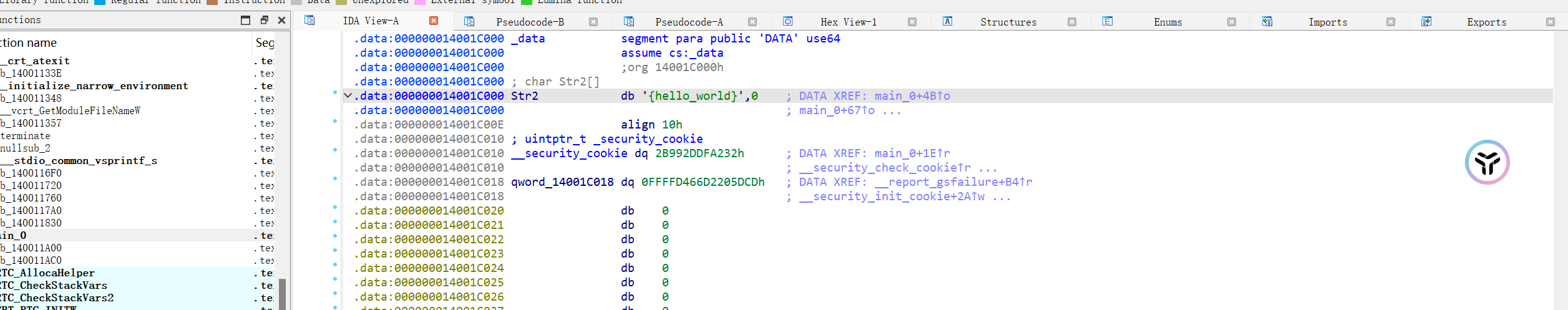
进入得到str2的值,即flag
然而这是初始的str2值,在主函数中,for循环对str2进行了处理,str2里面ascii码为111的字符会被转换为ascii码为48的字符

因此需要进行再次转换,得到flag, flag{hell0_w0rld}
reverse3
题目为exe文件
首先,放入exeinfo查壳

发现为32位程序,无壳
用IDA打开:
分析主函数:

其中,sub_4110BE函数实现了base64编码
sub_4110BE:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
| void *__cdecl sub_411AB0(char *a1, unsigned int a2, int *a3)
{
int v4;
int v5;
int v6;
int v7;
int i;
unsigned int v9;
int v10;
int v11;
void *v12;
char *v13;
if ( !a1 || !a2 )
return 0;
v9 = a2 / 3;
if ( (int)(a2 / 3) % 3 )
++v9;
v10 = 4 * v9;
*a3 = v10;
v12 = malloc(v10 + 1);
if ( !v12 )
return 0;
j_memset(v12, 0, v10 + 1);
v13 = a1;
v11 = a2;
v4 = 0;
while ( v11 > 0 )
{
byte_41A144[2] = 0;
byte_41A144[1] = 0;
byte_41A144[0] = 0;
for ( i = 0; i < 3 && v11 >= 1; ++i )
{
byte_41A144[i] = *v13;
--v11;
++v13;
}
if ( !i )
break;
switch ( i )
{
case 1:
*((_BYTE *)v12 + v4) = aAbcdefghijklmn[(int)(unsigned __int8)byte_41A144[0] >> 2];
v5 = v4 + 1;
*((_BYTE *)v12 + v5) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | (16 * (byte_41A144[0] & 3))];
*((_BYTE *)v12 + ++v5) = aAbcdefghijklmn[64];
*((_BYTE *)v12 + ++v5) = aAbcdefghijklmn[64];
v4 = v5 + 1;
break;
case 2:
*((_BYTE *)v12 + v4) = aAbcdefghijklmn[(int)(unsigned __int8)byte_41A144[0] >> 2];
v6 = v4 + 1;
*((_BYTE *)v12 + v6) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | (16 * (byte_41A144[0] & 3))];
*((_BYTE *)v12 + ++v6) = aAbcdefghijklmn[((byte_41A144[2] & 0xC0) >> 6) | (4 * (byte_41A144[1] & 0xF))];
*((_BYTE *)v12 + ++v6) = aAbcdefghijklmn[64];
v4 = v6 + 1;
break;
case 3:
*((_BYTE *)v12 + v4) = aAbcdefghijklmn[(int)(unsigned __int8)byte_41A144[0] >> 2];
v7 = v4 + 1;
*((_BYTE *)v12 + v7) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | (16 * (byte_41A144[0] & 3))];
*((_BYTE *)v12 + ++v7) = aAbcdefghijklmn[((byte_41A144[2] & 0xC0) >> 6) | (4 * (byte_41A144[1] & 0xF))];
*((_BYTE *)v12 + ++v7) = aAbcdefghijklmn[byte_41A144[2] & 0x3F];
v4 = v7 + 1;
break;
}
}
*((_BYTE *)v12 + v4) = 0;
return v12;
}
|
aAbcdefghijklmn是一个全局数组,用于存放Base64编码所对应的字符
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=
可以确定确实为base64编码。
由于最后使用strncmp函数比较Destination和Str2,我们进入Str2查找其值:e3nifIH9b_C@n@dH
得到Str2后,可以根据main函数的原理逆解出flag
总结主函数的基本内容:
输入flag——base64加密——赋值给v4——复制给Destination——for循环——与Str2比较
那么逆向解密:
1
2
3
4
5
6
| import base64
s="e3nifIH9b_C@n@dH"
flag=""
for i in range(len(s)):
flag+=chr(ord(s[i])-i)
print(base64.b64decode(flag))
|

得到flag
flag{i_l0ve_you}










